Breaking and Protecting Cryptographic Hardware: Power Analysis Side-Channel Attack and Mitigation
Cryptographic algorithms are mathematically secure. But cryptographic hardware isn't abstract math running in a vacuum. It's physical circuits consuming power, radiating electromagnetic fields, and taking measurable time to complete operations. These physical behaviors leak information about the secret keys being processed - letting attackers extract keys without brute force.
In a research project with UConn PhD student Jordan Cote, we implemented DES encryption on an FPGA, performed a successful power analysis attack to extract key information from power consumption patterns, and designed three countermeasures to defend against these attacks.
View Full Technical Report (PDF)
Implementation
The challenge wasn't just getting DES working on the Xilinx Spartan 3 FPGA. The implementation needed to be vulnerable enough to demonstrate the attack while remaining realistic enough to represent production systems. We used an open-source DES core in VHDL and added extra logic to exercise all pathways so the FPGA synthesis tools wouldn't trim unused circuits. A 64-bit counter fed the data input, and I recycled the output back to the key input to iterate through different keys. The result ran a 16-cycle encryption every 18 clock cycles.
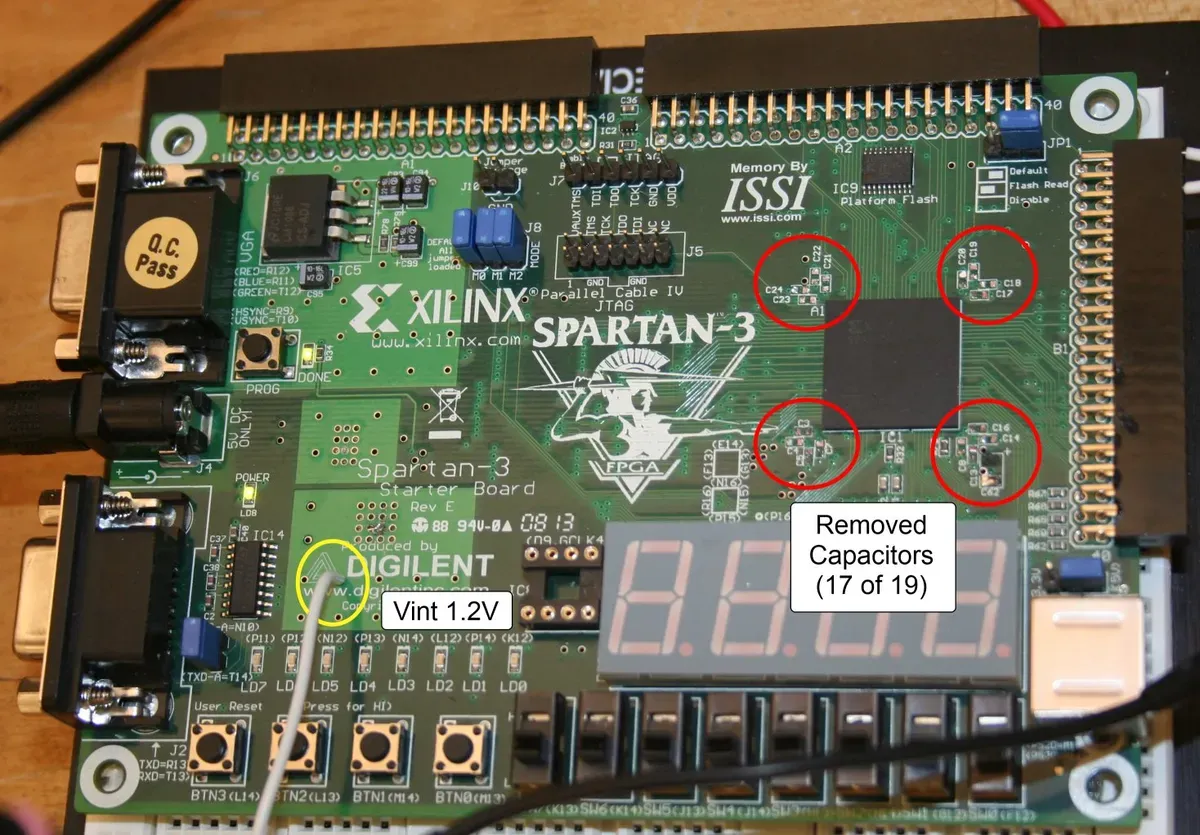
Xilinx Spartan 3 FPGA with 17 of 19 capacitors removed (circled in red) to enable power analysis
To measure power consumption, we removed decoupling capacitors from the board, bypassed the DC/DC converter, and added a 1.6Ω sense resistor between the external power supply and FPGA. A 300MHz Tektronix oscilloscope measured the voltage drop across the resistor.
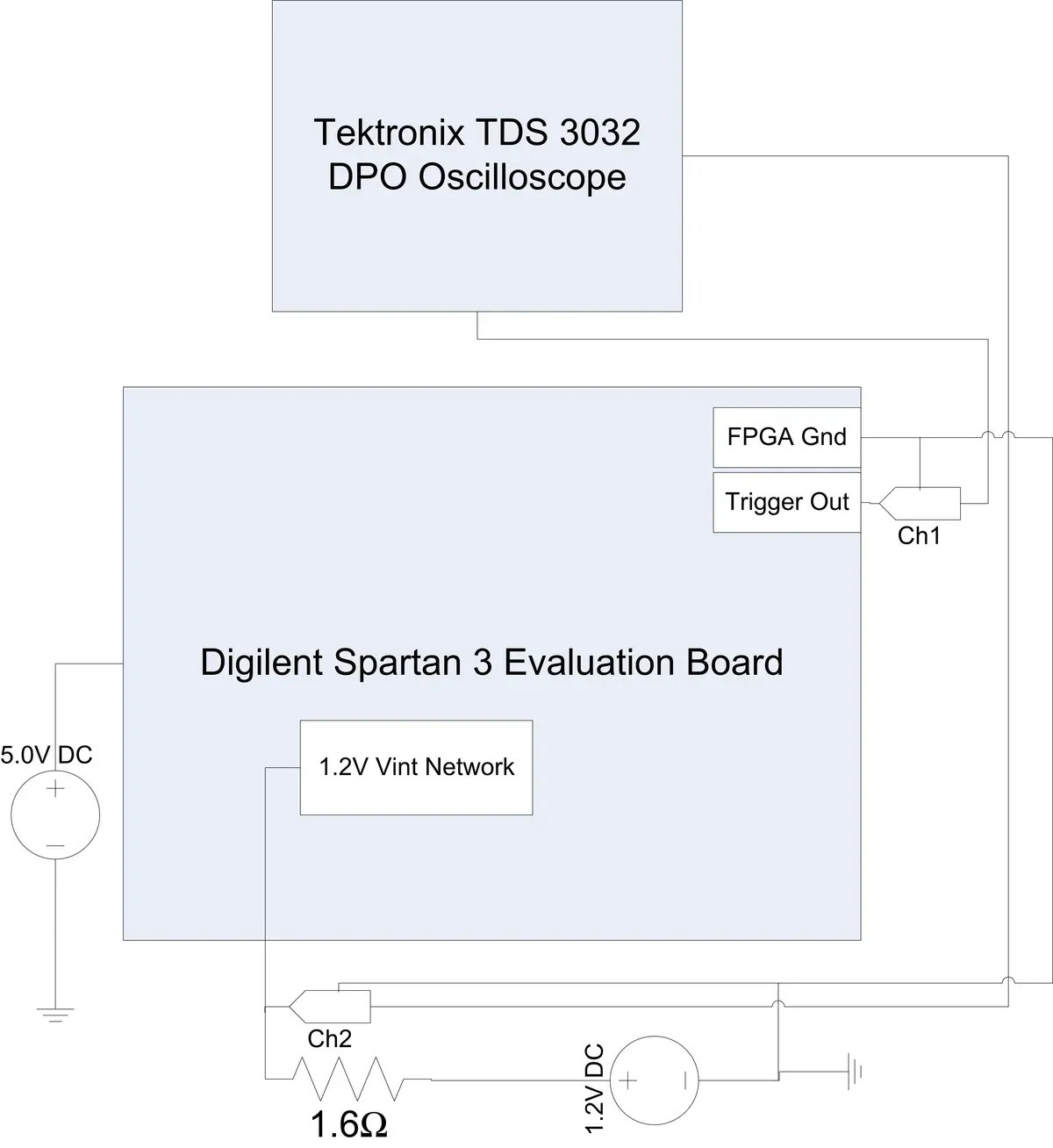
Experimental setup: External power supply, sense resistor for current measurement, and oscilloscope triggering
The Attack
With the oscilloscope triggering on the encryption completion signal, we captured power traces during DES encryption. The 16 DES rounds were clearly visible. Each round had distinct power consumption patterns, and consecutive encryptions with different keys showed measurable differences.
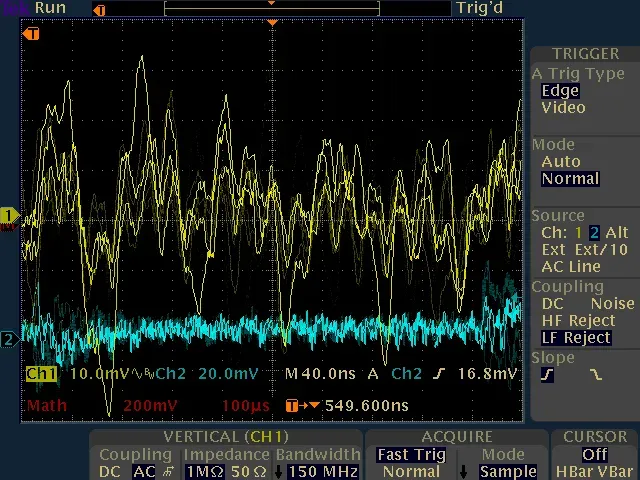
Simple Power Analysis persistence trace showing multiple DES encryptions.
The 16 rounds are clearly visible, with distinct patterns for different keys.
The attack worked for three reasons. DES rounds execute sequentially, creating distinct temporal patterns. Different keys cause different bit-flipping patterns, which means different power consumption. And removing the capacitors with a clean power supply made the signals remarkably clear.
Defenses
We implemented three countermeasures to obscure the power traces.
The first ran a second DES core on an inverted clock, encrypting on both rising and falling edges. This made the trace look more random and obscured individual round patterns. But the differences between encryptions might actually help a Differential Power Analysis attack.
The second ran a second DES core at one-third the main clock speed. This made the amplitude more consistent across rounds and made it harder to identify when the actual DES encryption started. The more consistent appearance should make DPA more difficult.
The third combined both approaches with a second DES core running at one-third speed on an inverted clock. The combined defense showed properties from both previous approaches and performed best overall.
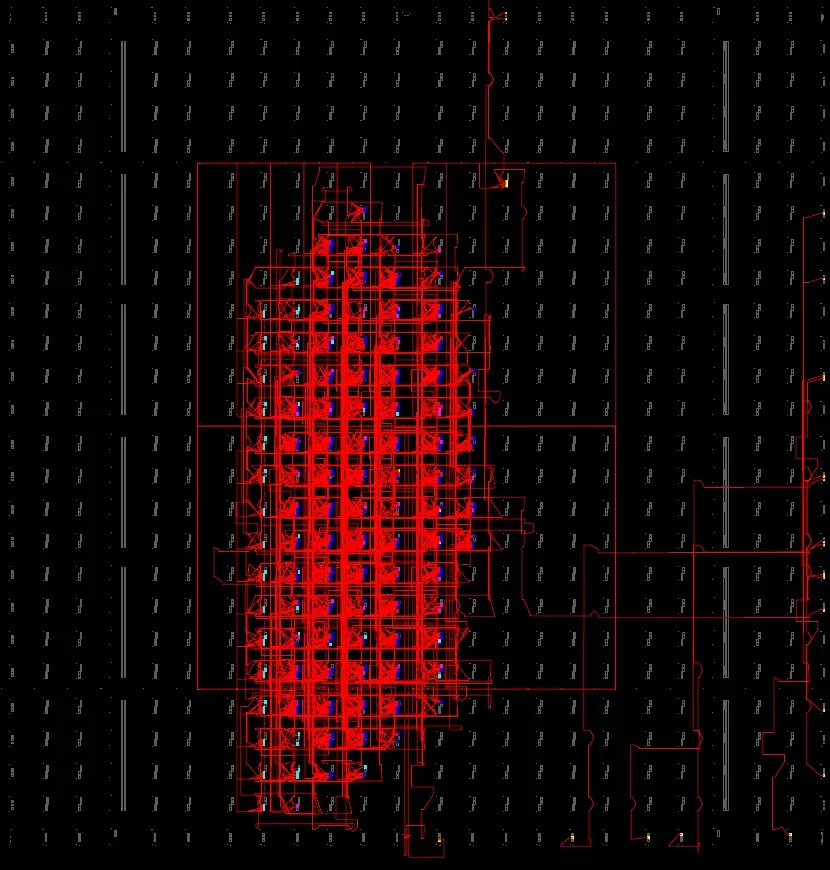
FPGA layout (Xilinx ISE) showing the DES core (red) with supporting logic and interconnects
What Worked and What Didn't
The attack demonstrated that FPGA parallelism doesn't prevent power analysis, contrary to what we expected. The physical modifications to the board made a huge difference in signal quality. But we also ran into practical measurement problems. Ground loops between the oscilloscope and voltage generator caused resets. The trigger signal carried so much noise that we couldn't trigger on the transition itself and had to use the voltage overshoot instead.
The defense mechanisms showed clear trade-offs. Randomization helps against Simple Power Analysis, but consistency helps against Differential Power Analysis. You can't optimize for both simultaneously.
Relevance to Later Work
Power consumption is a physical sensor signal, like accelerometer data or structural vibration. Understanding the physical system (how hardware executes operations) enables interpreting the signals more effectively. The pattern is: signal processing, pattern recognition, physics-informed modeling.
Security thinking carried forward too. A habit of thinking about information leakage through physical channels and analyzing attack surfaces was grounded in this research and graduate studies in digital hardware security with Dr. Mark Tehranipoor, a leading researcher in hardware security, trust, and supply chain security whose work on hardware trojans and counterfeit detection has shaped the field.
Technical Details
Hardware: Xilinx Spartan 3 FPGA (Digilent evaluation board), Tektronix TDS 3032 300MHz oscilloscope, external 1.2V voltage generator. Modified the board by removing 19 capacitors, bypassing the DC/DC converter, and adding a 1.6Ω sense resistor.
Software: Xilinx ISE 11.1 for VHDL design, ModelSim XE III 6.4b for simulation. Custom triggering logic using the data-ready signal alternation.
Algorithm: DES encryption (16 rounds, 64-bit blocks, 56-bit keys) with supporting logic including a 64-bit counter, register, and parity generator. Defense mechanisms used multiple DES cores with different clock variations.
I worked with lab partner PhD student Jordan Cote and was advised by Dr. Tehranipoor. The full 11-page technical report documents the implementation, attack methodology, and comparative analysis of the three defense mechanisms.
Resources
Full Technical Report (PDF) - Includes RTL schematics, FPGA layout, experimental setup diagrams, power traces, and comparative defense mechanism analysis.
